Spotting Cyrillic Homograph Attacks
Have you ever clicked on a link and thought everything seemed normal, only to find out later it was a scam? If so, you’re not alone. Many people fall victim to a sneaky phishing trick called a homograph attack. This technique swaps ordinary Latin characters with similar-looking Cyrillic ones to fool users into thinking they’re visiting a legitimate site. Today, such tactics are becoming increasingly sophisticated and prevalent. It’s vital to stay alert and know what to watch out for. With just a small change, hackers can redirect you to a website that looks genuine but is designed to steal personal information. In this post, I’ll walk you through the basics of these clever scams, so you can recognize the signs and protect yourself from becoming a target. Let’s dive in!
Understanding Homograph Attacks
Many of us have grown accustomed to trusting the URLs we click. Yet, beneath this surface lies a sophisticated internet scam named homograph attacks, which can deceive even the most cautious users. Let’s explore how these attacks work and why staying informed is so crucial.
Definition of Homograph Attacks
A homograph attack is a malicious practice where an attacker uses characters that look similar to those in a legitimate domain. By swapping these characters, often substituting Latin letters with those from the Cyrillic alphabet, they trick users into visiting bogus websites. For instance, the English letter “a” is nearly indistinguishable from the Cyrillic version. This creates the perfect setup for a phishing scam, where a user believes they are navigating to a trusted site but instead lands on a malicious copy designed to steal their information.
Historical Context
Homograph attacks have been part of the hacker’s toolkit for more than a decade. The first known incident was back in 2011, targeting a US television site through a cleverly registered domain. The goal? Spread an outrageous rumor about Idaho banning Justin Bieber’s music. Although it seemed almost trivial, it marked the beginning of a series of exploits using similar tactics. These attacks trace their roots to changes in how domain names are structured, specifically with the integration of Unicode. This allows characters from different scripts to appear identical, which hackers have skillfully exploited over the years.
How Character Confusion Occurs
It’s remarkable how such a small visual change—like the switch of a character set—can lead to significant deception. Cyrillic and Latin characters often appear so alike that they can be interchanged without drawing attention. When you see a URL using Cyrillic characters that mimic Latin ones, it might seem just like any other web address, yet it directs you to a fraudulent site. These attacks rely on our natural tendency to skim rather than scrutinize every character in a URL, and that tiny difference can make a world of deceit. Understand these mechanics better here.
Being aware of how this character confusion occurs not only empowers us to protect our online presence but also encourages a moment of thoughtfulness before each click.
Recognizing Phishing Attempts
Navigating the internet might feel like second nature, but staying vigilant against phishing scams is crucial. One crafty tactic involves swapping Cyrillic characters for Latin ones to create deceptive links that appear legitimate. In this section, we’ll look at how these characters compare and the warning signs to watch for when encountering phishing attempts.
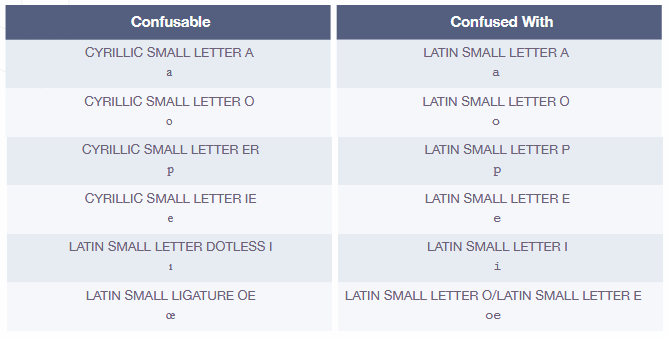
Cyrillic vs. Latin Characters
Some Cyrillic characters closely resemble Latin characters, making them a tool for trickery. Hackers exploit these similarities to craft domains that look just like familiar sites. Here are a few Cyrillic characters commonly mistaken for their Latin counterparts:
А (Cyrillic) vs. A (Latin)
С (Cyrillic) vs. C (Latin)
В (Cyrillic) vs. B (Latin)
Е (Cyrillic) vs. E (Latin)
You might think you’re accessing a legitimate URL, but a single Cyrillic letter can redirect you to a malicious site. To dig deeper into how these characters are used in phishing schemes, check out this in-depth article.
Warning Signs of Phishing Scams
Identifying phishing attempts is more about vigilance than expertise. Here are some red flags that can help you spot suspicious emails or websites:
Generic Greetings: Does the message start with “Dear Customer”? Personalized emails typically address you by name.
Urgency or Threats: Phrases like “Your account will be closed” or “Immediate action required” are classic phishing strategies to create panic.
Grammar and Spelling: Poorly written emails with obvious errors can signal a phishing attempt. Legitimate companies maintain professional communication.
Unfamiliar Senders: Is the email from a name or address you’ve never seen? Definitely worth a second look.
Mismatch URLs: Hover over any links. If the URL doesn’t match the company’s official address, steer clear. More information on recognizing these signs can be found in this guide.
Being proactive and inspecting these elements can shield your data from threats. Although the internet’s vast landscape has its dangers, a touch of skepticism can keep you safe from cyber deceit.
Protecting Yourself from Homograph Attacks
Navigating the digital world requires vigilance, especially when it comes to recognizing threats like homograph attacks. These phishing tactics prey on our habits of skimming through familiar URLs, hoping to catch us off guard. However, with a few proactive steps, you can arm yourself against these deceptive strategies. Let’s explore how you can stay safe online.
Using Security Software
In the age of digital deception, keeping your security software updated is akin to locking your doors at night—it’s the first line of defense. Cyber attackers constantly evolve their tactics, so using outdated software is like leaving the door ajar for them. Regular updates ensure that your devices are fortified against new threats. They patch vulnerabilities that hackers exploit and often include enhancements that improve functionality. I never ignore those update notifications; doing so might just save you from the next cyber attack. Find out why this is crucial.
Manual URL Verification
Spotting a fraudulent URL isn’t always straightforward, yet it’s a skill that can shield you from malicious sites. Before clicking on any link, take a moment to inspect it closely. Does it look odd? Are there unusual characters or slight misspellings? Trust your instincts if something seems off. Hover over links to preview where they lead. This simple habit might feel like a red light on a quiet street, but it’s a necessary pause that could prevent a digital collision. Here’s a useful tip on how to do it well.
Education and Awareness
The war against phishing isn’t won by tech alone; it requires informed users who recognize threats before they hit. Education is your best ally. Make it a point to stay updated on how these attacks evolve. Joining forums, attending webinars, or simply reading trusted tech blogs can offer insights into the latest phishing schemes. Remember, knowledge is your own personal shield. Explore these insights to stay ahead.
By adopting these practices, you’re not just protecting your devices but also creating a secure cyber environment for you and those around you. Each step counts toward a safer digital experience.
Conclusion and Final Thoughts
Navigating the web can feel like tiptoeing through a minefield, especially with the sneaky tactics of homograph attacks lurking in the shadows. These attacks, where Cyrillic characters replace Latin ones to create fake URLs, are a favored tool in the hacker’s arsenal. They exploit our natural tendency to trust what looks familiar and use it against us. It’s crucial to understand these tricks, so we don’t fall prey to them.
Key Takeaways
Staying safe from these tricksters involves a mix of awareness and action. Here are some key points to remember:
Understand the Threat: Homograph attacks utilize characters from the Cyrillic alphabet that look like Latin letters to create deceitful sites. Recognizing the subtle differences in URLs is vital. For more information, explore how these attacks work.
Spot the Red Flags: Be wary of URLs with odd characters or misspellings. Verify the source before clicking. It’s like double-checking the locks before leaving home.
Use Technology to Your Advantage: Employ updated security software to spot phishing attempts before they reach you. Here’s how to strengthen your defenses.
The Importance of Vigilance
Cybersecurity isn’t just about having the latest software; it’s about mindset. We need to stay alert and informed. The internet is a vast world with its fair share of pitfalls, but with vigilance, we can navigate it safely. After all, the best defense is being one step ahead. Learn more about staying vigilant.
By incorporating these strategies into our daily routines, we not only protect ourselves but also contribute towards making the digital space a little safer for everyone. Let’s stay informed, question the abnormal, and trust our instincts. These small steps can go a long way in safeguarding our digital lives.